
A new threat called “ransomware” has become increasingly notorious in recent years. This is computer malware which in its simplest form encrypts all or some of the victim’s data, denying access usually until the victim presents some form of payment. Ransomware is cropping up in many different environments, with education being a new hotspot vector. It can be acquired through email attachments, fake software upgrade downloads, peer-to-peer platforms, propagated via external drives, etc.
Below is an example of the message a user might receive once infected:
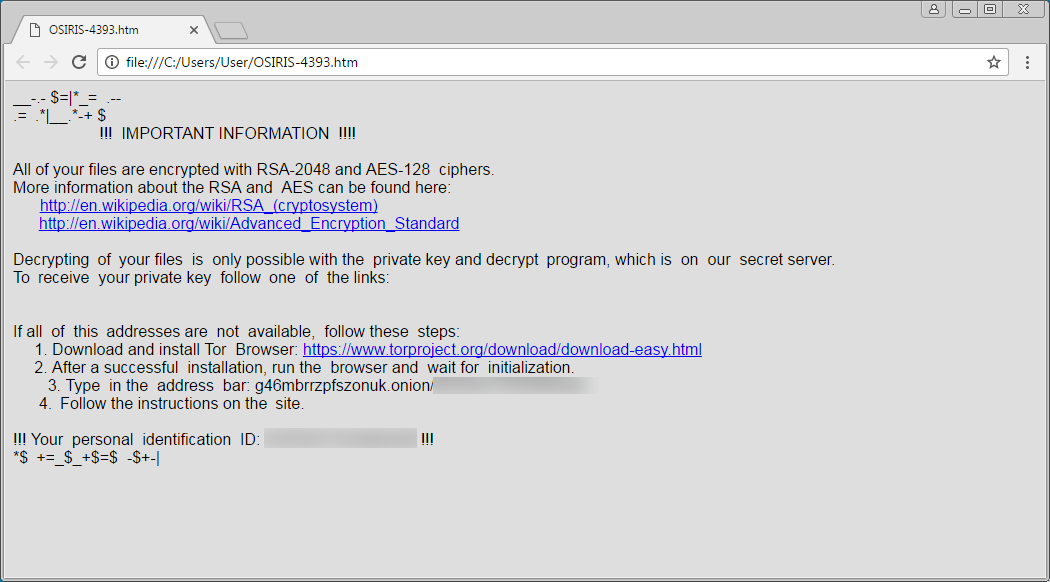
Payment has traditionally been requested through the Bitcoin medium, and full decryption of the files is never guaranteed once payment is received by the attacker. This makes ransomware tough to recover from once affected.
Following the trend of any thriving tech entity, ransomware has become increasingly sophisticated in its packaging, execution, and its “bargain” requirements for the hostage data to be released. Below is a closer look at just a few of the new flavors that have been observed in the past year:
Zcryptor
Zcryptor drops a file labeled autorun.inf on any removable drive (e.g. usb flash) that is mounted on the infected computer. It therefore self-propagates, exhibiting worm characteristics.
“The ransomware targets numerous file types, encrypts them and adds the .zcrypt extension to them, while also creating the zcrypt1.0 mutex on the infected machines, which is meant to denote that an instance of the malware is already running. The ransomware also connects to specific servers to exchange information with them, but researchers say that these servers were inactive during their analysis.”
From <http://www.securityweek.com/zcryptor-ransomware-spreads-removable-drives>
Locky
A close cousin of Zcryptor, Locky is known to also encrypt files on network shares that the infected user has permissions to. This one is initiated when the victim opens a Microsoft Office document and enables macros for that document. This kicks off a script which encrypts most of the files in the user profile in just minutes, along with any attached peripheral drives or network shares they are permitted to access. The malware is fairly good at covering its tracks too, removing any executables it creates under the hidden %AppData% folder, as well as changes and additions to the Windows registry.
“Remember also, that like most ransomware, Locky doesn’t just scramble your C: drive. It scrambles any files in any directory on any mounted drive that it can access, including removable drives that are plugged in at the time, or network shares that are accessible, including servers and other people’s computers, whether they are running Windows, OS X or Linux.”
From <https://nakedsecurity.sophos.com/2016/02/17/locky-ransomware-what-you-need-to-know/>
Doxware
This one takes the traditional ransomware attack a big step further by threatening to release private information (personal or organizational) to the public. This includes private conversations, photos and other sensitive information, and only increases the pressure on the victim to pay the ransom. Due to the in-depth nature of this attack, DarkReading suggests that attackers would likely use this for more specialized targets.
“Doxware requires strategic end-to-end planning, which means hackers will target their victims more deliberately. Therefore, malicious players will be more intentional in whom they attack, giving corporate leaders, politicians, celebrities, and other public figures cause for concern.”
Popcorn Time
This is actually considered a mutation of “Doxware,” but the requirements to decrypt become even more interesting. With a cynical twist on the “word-of-mouth” marketing approach, the victim can choose to infect two of their affiliates in lieu of paying the ransom.
Database Threats
Folks over at BinaryEdge have seen a surge in ransomware hitting a handful of database technologies, including MongoDB, Redis, ElasticSearch, Hadoop, Cassandra and CouchDB. Click here to access their blog and read more on this.
How Do I Get This, and What Can I Do To Prevent?
Be Cautious with Software Updates and Download Prompts: Ransomware and other types of malware have a knack for getting in via fake software updates; Adobe Flash sits at the top of this list. Avoid using these pop-ups and prompts as a medium to acquire downloads. If you feel that you are due for an upgrade, visit the official site of the corresponding product to download. Most software also offers you the ability to see the current version and check for updates from its main menu.
Be Careful with Unsolicited Attachments: Know your email senders. If something looks suspicious, your best bet is to assume that it is. Trust me, it is well worth the time cost of an extra minute or two to verify something that could do some serious damage to you or your organization if infected. Visit or call the IT Service Desk at 860-439-HELP (4357) if you have any questions or would like to further investigate an email message.
Back Up, Back Up, Back Up: The best thing you can do to work against these threats is to back up your data regularly. Many flavors of ransomware actually disable the built-in VSS (Windows Restore) services on the machine during the time of infection, so it is important to back up your critical data frequently to a cloud service or some form of external drive. All users in the conncoll.edu domain have unlimited storage in Google Drive, making this a favorable option.
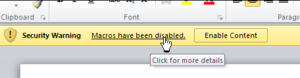
Do not enable Macros: Microsoft turned off auto-execution of macros by default many years ago, and for good reason. If you or your department needs a particular macro, please call the Service Desk or Information Security office to verify the legitimacy of a particular macro or file type. Also, take a look at the document you just opened before hitting that “enable” button (shown below). The contents of the document can tell you it is not what you were looking for or what you expected, and you should close out and remove the file altogether.
NOTE: Remember that the biggest vector for all computer-related attacks is you, the human. Hackers of this decade are carefully analyzing social behaviors and engineering their delivery in ways that exploit these behaviors. In a society that heavily favors social media and the immediate public sharing of even the smallest ideas, people have become significantly more trusting. In order to stay protected it is important to think carefully, ask questions and educate yourself.

One thought on “The Rise of Ransomware”